An Analysis of AuthO for Authentication
Executive Summary
- This is an analysis of AuthO, which is a service for authentication.

Introduction
This is a good way to begin this article.
Authentication is a complex topic, if you think otherwise you will probably get burnt down the road. There’s a myriad of technologies, protocols, concepts and do’s and don’ts. On top of that it’s difficult to keep track of all the evolving best practices and outdated/overloaded terminology; the last one is especially troubling if you’re just getting started on the subject and start to see different things being called by the same name or the other way around. – The Authentication Survival Guide
Most membership plug ins leverage WP’s standard user functionality. One problem with this is that this user functionality is how bots hack WP websites. We have a large number of bots that probe and try to break into Brightwork Research & Analysis on a daily basis. Because of this, we have used WP Cerber to shut down anyone but us from being able to login to the website.
AuthO
There is a combined service called AuthO. Another similar one is called FusionAuth.

It is $23 for 1000 users and can be scaled up. Expensive levels don’t really come until the pro version of AuthO is used.
AuthO runs on top of AWS and is an AWS Startup, so it is not necessary to “host” AuthO.
Why AuthO Runs on AWS
This is covered thusly.
Ready to have your identity wired and running in minutes or at most days (for most common use cases)?
This is why Auth0 and AWS work together to ensure that AWS customers can have the quick, easily implemented identity solution they need for their specific application.
AWS has a number of cloud-scale security services built into its platform that simplify building and operating an advanced security architecture, including: Fine-grained and ephemeral access control through IAM roles Encryption services (including key management and data encryption) Detailed audit logging, Cloud scale network defense services with Guard Duty and AWS Shield.
Using IAM has enabled us to enforce the principle of least privilege, transparently restricting our engineers to only the resources they require to perform their role. Users receive short-lived access to perform the approved action and refresh their access periodically allowing us to move away from static long-lived credentials. The encryption services that AWS provides allow us to implement critical encryption controls at scale with low friction for Security and engineering teams. The AWS Key Management Services (KMS) is a fips-140 validated key store that has allows us to protect and rotate our keys. And, services such as The Elastic Block Store (EBS) encryption allows us to encrypt all our data at rest by default without managing our own infrastructure. – Why AWS & AuthO?
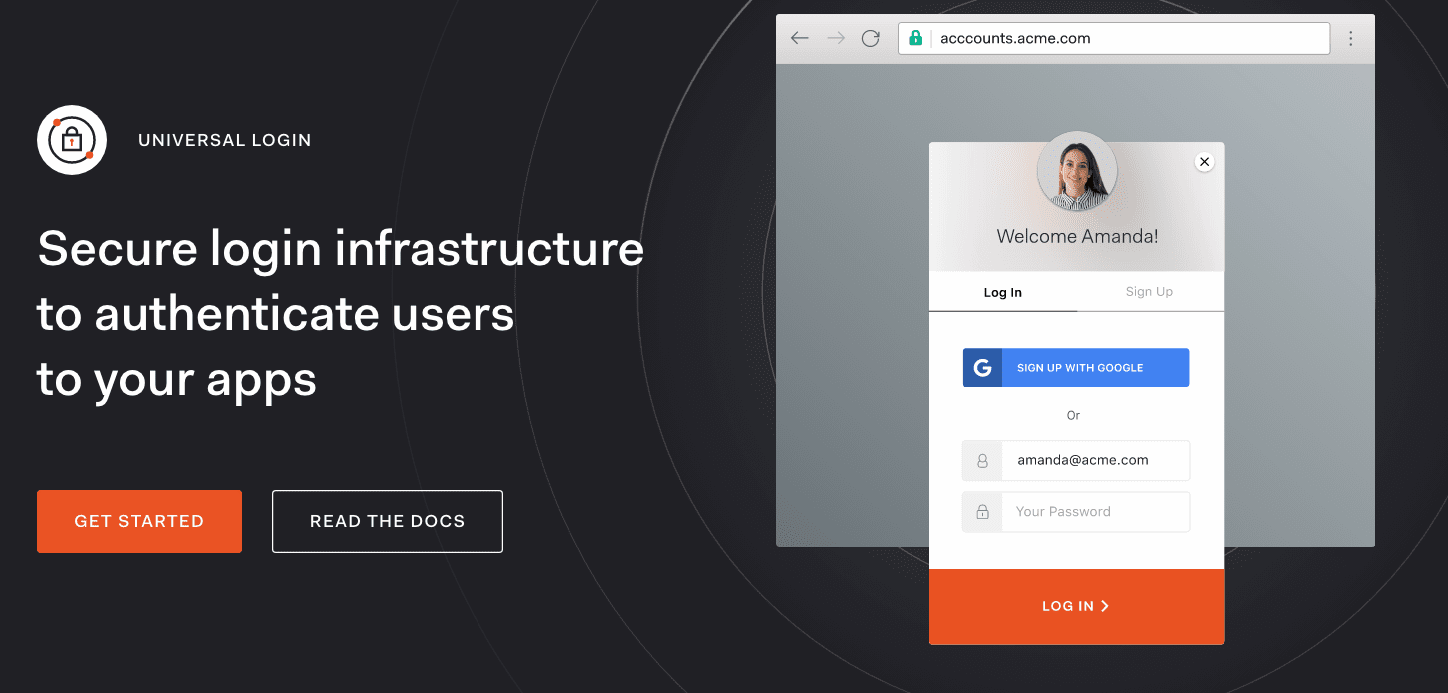
With Universal login, users are redirected to a central authorization server. Because authentication is taking place on the same domain as the login, credentials are not sent across origins, increasing security and protecting against attacks such as phishing and man-in-the-middle. – AuthO
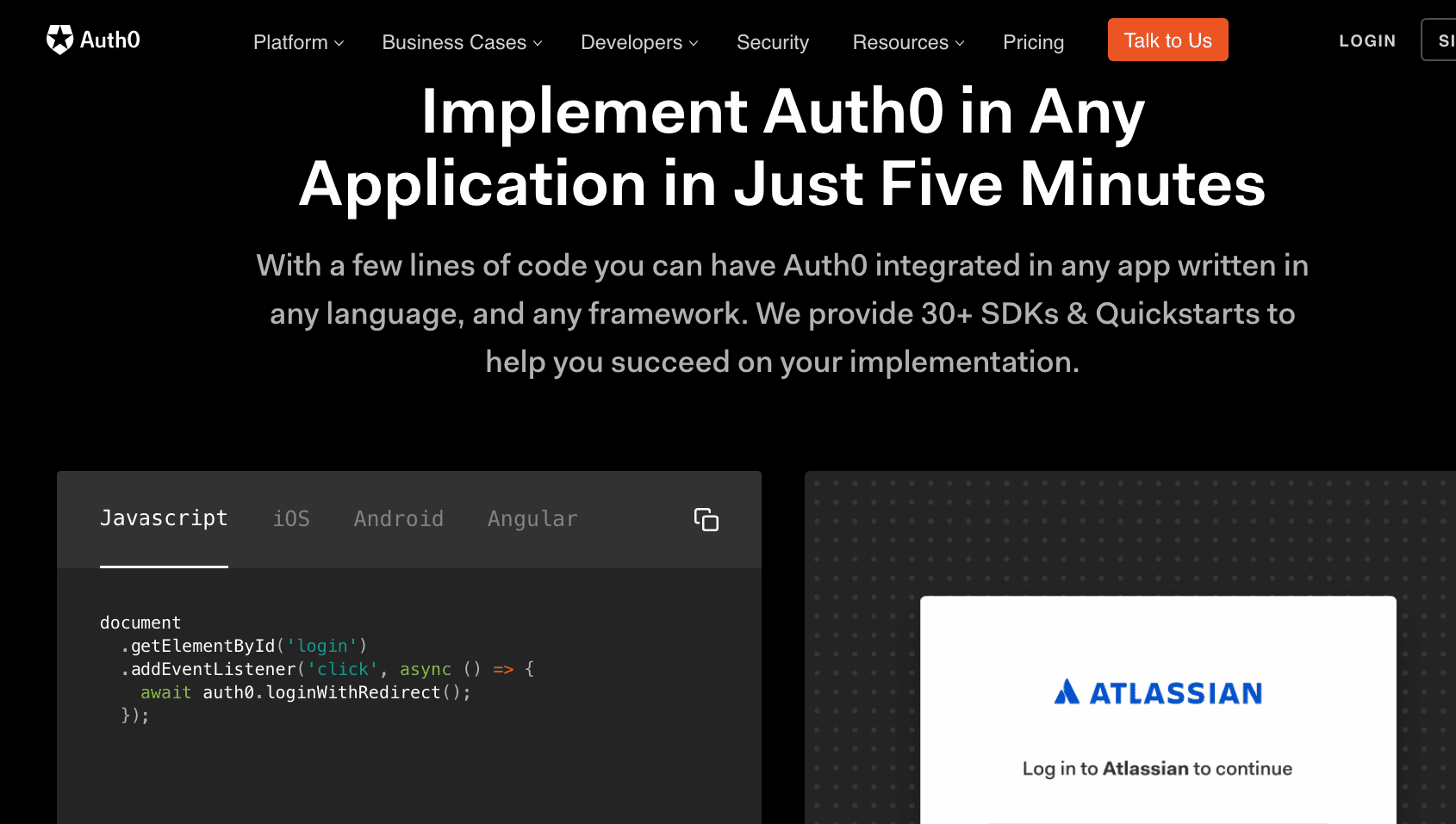
This is curious and interesting, it shows that code is installed on the pages, rather than trying to integrate with (in this case WP) through a plug in.
Let us review the code.
document
.getElementById('login')
.addEventListener('click', async () => {
await auth0.loginWithRedirect();
});Notice this tells the browser to redirect to the authO server. This is where the quote applies..
in any app written in any language, and any framework.
In this case, WP is the framework. This means that AuthO can be inserted in just ordinary HTML pages, or in an WP page.
There is a header and footer code entry, which means that this code could be entered there, if it could be configured at the AuthO server which pages were protected and which were not. That would be nice — but if not, then the code would be entered into only those pages in the WP instance that needed to be protected.
Notice this quotation.
“Our engineers don’t have to build the interfaces, they don’t have to build all the security around it, … they don’t have to deal with managing any usernames or passwords. It’s all taken out of our hands.” – Scott Scherer
The Motley Fool and the Economist both use AuthO. These are of course content providers that require membership management.
I signed up for AuthO’s free trial account.
Conclusion
AuthO is a recent startup, but has already become extremely popular.
For example, OAuth, which is part of AWS Startups, is only around a year old as of this publication.
References
https://auth0.com/docs/extensions/custom-social-connections?_ga=2.151476089.1310177507.1597800031-2059069436.1597800030&_gac=1.94884334.1597800031.Cj0KCQjw-O35BRDVARIsAJU5mQWBwrXePLRDrTKYJmvJ7lmvSNUMdLax_zTeTOTBEXqtY-OGYA_TGp4aArUqEALw_wcB
https://assets.ctfassets.net/2ntc334xp5/57svSdnx07lHKIjdyzhDVL/ccb7df4cced46b84556039d57f3d1b87/20191112_Why-AWS-Auth0__1___1_.pdf
https://assets.ctfassets.net/2ntc334xp5/5XSndKseXucycEAg6cGAOo/36c8041aa685a624dd5af0431b190cf8/data-playbook.pdf